Cybersecurity regulations: which ones must your company comply with?
Cybersecurity regulations emerge as one of the logical developments in today's hyper-connected business world.
As cybercriminals advance their capabilities to generate disruptive events, the responsibility of organizations to protect their activities and the data they safeguard becomes essential. Thus, public authorities and the standardization of cybersecurity governance measures lay the foundations for organizations to become true defensive bulwarks in a digital environment where cyber threats are reaching record levels of impact.
In this context, we review the main cybersecurity regulations impacting companies globally and provide a roadmap to effectively navigate these requirements.
6 cybersecurity regulations that apply to companies
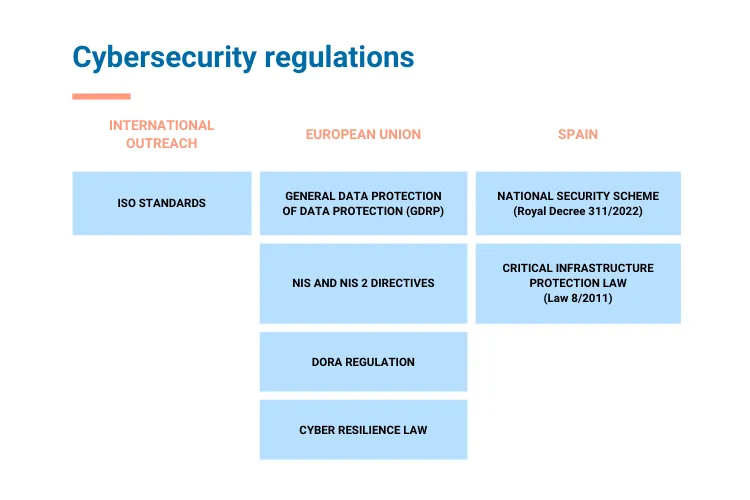
ISO Standards
Set of standards developed by the International Organization for Standardization, a worldwide reference in this area dedicated to regulating a multitude of processes and industries beyond cybersecurity. Complying with ISO standards is synonymous with differentiation, as it demonstrates a commitment to globally recognized high standards whose compliance is also evaluated by an external certification body.
As far as cybersecurity standards are concerned, it is necessary to look at the ISO 27000 family, a series of standards whose objective is to implement an Information Security Management System (ISMS) in organizations. In turn, within this set of standards, the following stand out:
ISO 27001
Provides the main requirements for implementing, improving and maintaining an ISMS based on the PDCA (Plan, Do, Check, Act) cycle.
To this end, it establishes 93 security controls that organizations must implement according to their needs and objectives. These controls refer to various aspects divided into 15 operational capabilities, ranging from cryptography to information security policies and communications security, among others.
ISO 27017
As additional measures in the ISO 27001 standards package, this standard refers to the particularities of information security controls for cloud services.
The particularities of cloud cybersecurity are thus recognized. On the one hand, aimed at cloud service providers, the standard sets out a series of requirements to ensure that stored data is managed securely in processes such as data delivery or deletion.
It also offers a roadmap for organizations that contract this type of services, as it determines the controls that must be taken into account to make use of them with guarantees.
ISO 27018
Referring to the protection of Personally Identifiable Information (PII) in the cloud, it establishes standards relating to aspects such as consent and choice, data minimization, limit of use and liability.

GDPR (General Data Protection Regulation)
The General Data Protection Regulation is a European regulation implemented through local data protection laws in various countries, ensuring compliance with digital rights and data privacy standards, which represents a significant advance in the way in which personal data is protected in the EU, which responds to the need to deepen the active protection of the privacy of citizens of the Union, strengthening the privacy rights of individuals.
In this context, without any doubt, the greatest innovation of the GDPR was the introduction of the principle of proactive liability, as the need for the Controller to implement appropriate technical and organizational measures, in order to ensure and be able to demonstrate that the processing is in compliance with the Regulation.
With the introduction of this principle of proactive responsibility, data protection in the EU incorporates a risk-based approach to the protection of personal data, as it requires a consistent and careful attitude on the part of data controllers in all processing operations they carry out.
The new features of the GDPR do not end with this change in the approach to responsibility, but materialize in the following aspects of data protection:
- Legitimation of processing: new bases for legitimizing the processing of personal data are introduced, displacing consent as the main basis for processing.
- Rights of individuals: the GDPR strengthens the protection of the privacy of individuals, adding to the rights of access, rectification and erasure of personal data, the rights of limitation of processing and data portability.
- Data breach management: the GDPR has introduced the duty to inform the data protection authorities and the individuals concerned in the event of a data breach that may result in a high risk to the rights and freedoms of individuals. Effective security breach management will enable Data Controllers to understand the consequences of the security breach for the individuals whose data has been affected, to develop technical and organizational security measures to prevent future breaches as far as possible, to weigh up the advisability of incorporating them and to prevent the incident from recurring.
- Data protection by design and by default: Organizations must take data protection into account from the start of any processing process and ensure that appropriate measures are implemented to guarantee the privacy of individuals.

NIS2 Directive: Strengthening Cybersecurity Across the European Union
The NIS2 appears as a new cybersecurity directive in the European Union, and was created with the aim of ensuring a high level of cybersecurity by both public and private organizations belonging to certain sectors at European level.
This cybersecurity regulation is aimed at generating a true culture of cybersecurity in the European territory, in addition to eliminating the differences between member states regarding the security of networks and information systems. Among its most important measures are:
- It requires member states to take measures such as the creation of a national authority linked to cybersecurity, a cybersecurity incident response team (CSIRT) and a national cybersecurity strategy.
- Encourages the creation of a Cybersecurity Cooperation Group among the different member states.
- It establishes specific cybersecurity requirements for certain entities (detailed in the annexes), considered essential and important, such as energy, financial market or health sector. In these cases, the adoption of cybersecurity governance measures, risk management, and measures for the prevention and minimization of the impact of possible cyber incidents, in addition to the obligation to notify the occurrence of those of significant impact to the competent authorities, are urged.
As of October 2024, the transposition of the NIS2 Directive into the legal system of each of the member states will take place.

DORA Regulation
The DORA regulation is a European legislation initiative aimed at regulating cybersecurity in the financial sector. To this end, it establishes a series of obligations that seek to shield entities in this sector from growing cyber threats. Entities such as banks, fund managers and insurance companies, among others, are affected by this regulation. This regulation seeks to achieve a high common level of digital operational resilience by establishing uniform requirements for the security of the networks and information systems that support the business processes of these entities.
The main requirements established by DORA are:
- Entities bound by DORA must have in place a comprehensive risk management system, of which digital operational risk management (DRM) will form part , resting on a comprehensive ICT-related risk management framework . Organizations must make an exhaustive effort to identify their critical assets, assess the risks they face and put in place the necessary measures for their protection. All this guided and defined from the management body of each entity, which is established as responsible for compliance with applicable cybersecurity regulations. Within this framework, obligations are also established with respect to third party risk management through contractual agreements; and the need to carry out tests for the detection of vulnerabilities and penetration tests, among others.
- Entities are obliged to monitor possible incidents and inform the competent authorities and any interested party (including customers and partners) about serious incidents. To this end, they must permanently monitor and control the security and operation of their ICT systems, promptly detect anomalous activities and implement a global continuity policy.
- Encouraging collaboration between entities in the fight against cybercrime, through the figure of information and intelligence sharing agreements. Digital operational risk management will be fed by the information gathered by the entities on vulnerabilities and incidents, which must have crisis communication plans that allow the dissemination of this information to the rest of the system operators.

Cyber Resilience Act
The Cyber Resilience Act is another European initiative that seeks to complete the scope covered by cybersecurity regulations in the territory. In this case, it is aimed at regulating products with digital components, by introducing a series of mandatory cybersecurity requirements that must be applied during the product's entire life cycle.
This regulation generates a framework of requirements for the design, use and maintenance of this type of products, which manufacturers must comply with in European territory.

Country-Specific Regulations
Many countries implement national cybersecurity frameworks to ensure trust in digital public services. For example, in Spain, the National Security Scheme (ENS) plays a critical role in securing government-related digital services. Other countries may have similar frameworks to protect their public sectors and critical infrastructures.
The ENS in Spain, updated through the Royal Decree 311/2022, applies to public and private entities providing services to public administrations. It requires entities to have a cybersecurity governance model, incident management protocols, and business continuity measures in place.
How to address compliance with cybersecurity regulations for organizations.
We have reviewed the main cybersecurity regulations that organizations should be aware of. Some laws apply only to specific sectors, while others require compliance across all industries.
Compliance has become complex as regulations evolve alongside cyber threats and the technologies used to combat them. To achieve and maintain compliance, organizations must commit fully to demonstrating their adherence to cybersecurity standards.
This is where the expertise of compliance specialists becomes essential. At S2 Grupo, we help companies ensure compliance with global cybersecurity regulations through our Governance, Risk, and Compliance solutions. We design Cybersecurity Master Plans that elevate and maintain the security posture of organizations over time, addressing organizational, technical, physical, and legal aspects.
We also offer consulting and auditing services to help organizations comply with applicable laws in their jurisdictions. For example, we guide companies through national frameworks, such as the ENS in Spain, and help them achieve compliance with international standards like the GDPR or other relevant legislation.
Want to know more about how to comply with cybersecurity regulations in your organization? Contact us and find out how we can help you.
