What DDoS attacks are and how to avoid them
DDoS attacks stand out as one of today's key threats, with an increase in this type of incident in the first quarter of 2024 in Spain.
This boom in distributed denial of service in Spain can be understood, on the one hand, by the context of the conflict in Ukraine and the attacks activated by pro-Russian cybercriminals. In turn, DDoS attacks linked to hacktivism also play a significant role.
In this context, it is essential to understand what denial-of-service attacks are, how they work, and how to protect yourself effectively.
What are DDoS attacks?
DDoS attacks (Distributed Denial of Service attacks) are a type of security breach that seeks to overload network resources, websites, or servers, causing them to collapse and preventing normal functionality.
The attack is based on sending a massive amount of requests (traffic) to the target resource, exceeding its capacity to handle them. The result is the blocking of the target (website, systems, etc.), preventing users from accessing it.
The acronym DDoS is derived from the English term Distributed Denial of Service, i.e., “distributed denial of service attack.”
It is a type of cyber-attack capable of rendering large platforms unusable, with significant reputational and economic consequences.
The damage caused by DDoS attacks should not be underestimated, especially given that strategically perpetrated attacks can multiply their scope.
For instance, in October 2016, Dyn, a DNS company, was attacked with a massive DDoS. This attack, carried out by the Mirai botnet, infiltrated IoT devices (such as cameras and routers) to achieve its goal. It managed to bring down a multitude of major global web services and platforms, including X, Reddit, Netflix, and Spotify, rendering them inaccessible for several hours.
How a denial-of-service attack happens
A denial-of-service attack can use various techniques, but its core lies in flooding the server with requests to overwhelm its resources.
In the case of distributed denial of service, a botnet is created, multiplying the attack’s capacity to send massive requests. These bots are devices connected to the network (from computers to IoT or mobile devices) infected with malware, allowing them to propagate and spread the attack under an attacker’s instructions.
Once this network is created, the attack is launched by sending requests to the target resource, aiming to block it.
The attack works because network resources (such as servers supporting a web page and connection channels) have limits on the number of requests they can handle simultaneously.
Target of DDoS attacks
DDoS attacks primarily aim to disrupt the operation of their target (e.g., causing a website or application to “crash”). Even if they don’t achieve this goal, such attacks impact access speed, blocking legitimate traffic.
The consequences of denial-of-service attacks are multifaceted:
- Economic losses: This type of action often leads to economic losses. For instance, in e-commerce, DDoS attacks can prevent purchases on the portal, while attacks on internal resources may block employees from accessing emails or digital platforms.
- Reputational damage: The attack disrupts the experience for users visiting the website or application and can harm the organization’s credibility by exposing cybersecurity vulnerabilities.
- Ransom demands: The attacker may request payment to stop the attack, allowing the resource to be used again.
While DDoS attacks can occur in various contexts, they have become a favored tactic among hacktivist groups and are often employed in cyber warfare, extortion schemes, business competition, or even as entertainment by hackers testing system vulnerabilities.
How to mitigate DDoS attacks?
Law enforcement actions against cybercriminals launching DDoS attacks help curb these groups, but this is a reactive and limited measure.
Advances in detecting and mitigating this type of cyber threat now enable organizations to set up essential defenses.
We can mention four specific prevention and mitigation measures for denial-of-service attacks:
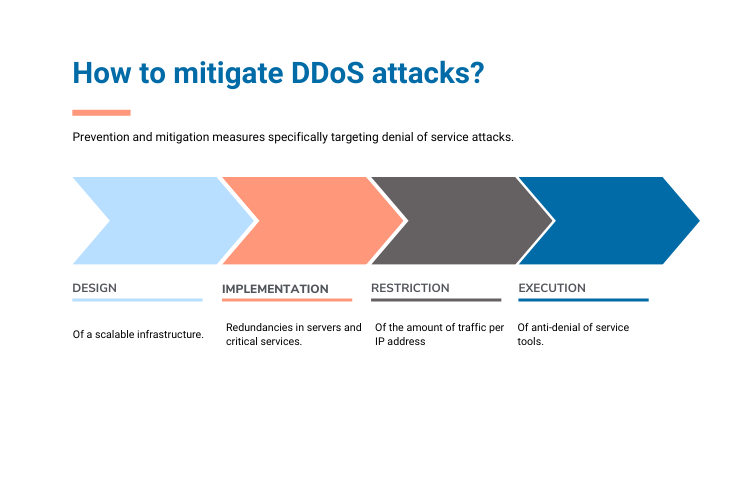
- Scalable infrastructure design
- Implementing redundancies in servers and critical services
- Limiting traffic per IP with filters and rate limits
- Using anti-DDoS tools at layers 3, 4, and 7
Beyond these technical measures, S2 Grupo, with two decades of experience, designs DDoS attack mitigation strategies based on key pillars:
- Geopolitical context analysis: Since denial-of-service attacks are often linked to hacktivism and cyber warfare, understanding these actors and their methods gives a proactive advantage. Knowing the behaviors and patterns of these groups is essential in defending against their attacks.
- Constant threat modeling: This involves analyzing an organization’s sector, geographic presence, assets, supply chain, and network vulnerabilities to identify potential weak points that attackers could exploit.
Effective protection against distributed denial of service involves a comprehensive strategy. This means dedicated efforts to minimize the likelihood of network and system compromises and intrusions. Ransomware and data breaches join DDoS attacks as prominent threats in today's digital space.
Effective defense requires addressing cybersecurity on multiple fronts, including:
- Network monitoring, detection, and blocking tools, along with data monitoring, collection, and analysis.
- Proactive cyber threat analysis methodologies.
- Defined intelligence cycles based on the organization’s needs.
- Integration of tools that allow detection of highly sophisticated threats, known as Advanced Persistent Threats (APT).
- Comprehensive vulnerability analysis.
- Coordinated action plans.
- Security assessments based on regulatory requirements.
- Cultivating a cybersecurity culture within the organization, creating a human barrier against digital threats.
At S2 Grupo, we assist organizations in protecting themselves against threats such as DDoS attacks and beyond, by developing effective cybersecurity strategies.
With over 20 years of experience and a team of more than 700 specialized professionals, S2 Grupo stands as a leader in cybersecurity and cyberintelligence across Europe and Latin America.
Our continuous commitment to innovation and in-house technology enables us to provide advanced solutions tailored to each client's needs, resulting in a secure and resilient infrastructure in today's evolving digital landscape.
Want to learn more about DDoS attacks, cybersecurity trends, and how to protect your organization through a comprehensive cybersecurity strategy? At S2 Grupo, we can help you.
