Threat modeling: keys and techniques
Although threat modeling is a technique directly linked to current technology and cyber threats, it is possible to understand it by drawing comparisons with defense methods that have been known since ancient times.
In this sense, since time immemorial, human groups seeking to protect specific locations have acted in two ways: examining their weak points in the face of an attack (possible entrances, angles from which there is no visibility...) and implementing strategies to mitigate these vulnerabilities (building walls, posting guards...).
Applied to the current technological context, this is precisely what threat modeling is capable of doing. Let's take a look at it.
What is threat modeling?
Threat modeling is a method and a set of processes that seek to identify and mitigate the potential vulnerabilities of an application or a set of digital assets.
To do this, threat modeling is based on three fundamental steps:
- To make a diagram of the architecture of an application.
- Identify possible weaknesses and quantify potential threats.
- Establish strategies to mitigate them effectively.
In this sense, it is a matter of carrying out an exhaustive analysis that makes it possible to anticipate specific cyber threats that could affect an asset and stop them from a preventive perspective.
Threat modeling can be applied to any IT infrastructure, and is also a paradigmatic process in the development of secure software by design.
Threat modeling objectives
- Determine the attack vectors in the IT architecture that could be exploited, including the critical components or assets whose exploitation would have the greatest impact.
- Mapping the specificcyber threats that compromise an application, including both malicious actions and accidents. Both the probability of the threat occurring and the assessment of its impact, i.e. the degree to which a threat can be considered critical, must be taken into account. In the case of threat modeling applied to IT infrastructures in the context of an organization, this also involves taking into account the organization itself, its priorities and the function of each asset.
- Establishment of security measures capable of mitigating these vulnerabilities in a preventive manner. Both compliance with the security requirements of the system itself and the applicable cybersecurity laws come into play here. Threat modeling can also generate a prioritization scheme for these measures, so that those considered critical are prioritized.
- Validation of securityprocedures, verifying that they are effective for the cyber threats detected and the asset or system to be protected.
- Providing comprehensive visibility into an application or asset and the potential vulnerabilities and threats, in addition to the cybersecurity measures in place. This results in a systematic improvement of an organization's cybersecurity posture by enabling professional collaboration, information sharing and data-driven decision-making and objective analysis.
In short, threat modeling is one of the fundamental pillars for generating truly effective security controls that also support a proactive and continuous cybersecurity culture over time.
The stages of threat modeling
Although different threat modeling methodologies (detailed in the next section) often propose their own stages, the basic outline for a well-thought-out threat modeling process is as follows:
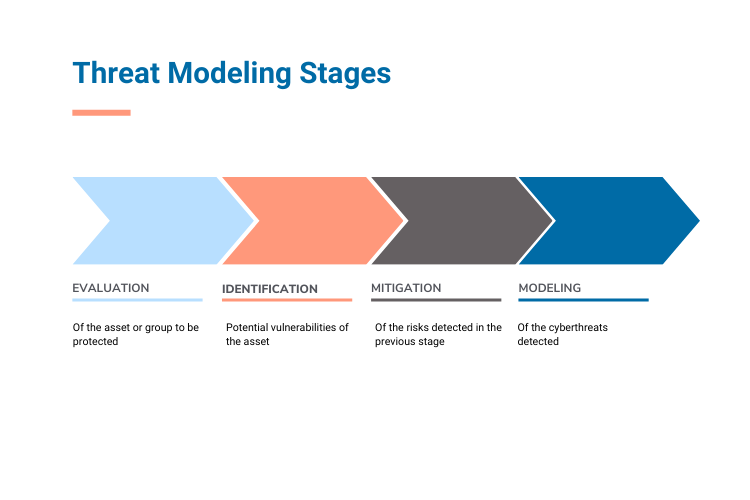
1. Evaluation
First of all, total visibility of the asset or set of assets to be protected is sought. This is the moment when fundamental tools come into play, such as data flow diagrams (DFDs) or data flow diagrams, which allow any system and the different data interactions to be modeled visually.
In this first evaluation step, the following elements must be taken into account:
- Components of an application (servers, libraries, gateways, interfaces...). Aspects such as sensitive data and critical components are determined here.
- Connections between components (data exchange protocols, encryption protocols, etc.). The data paths (their routes between components) and the entry and exit points of the trusted zone are made explicit.
The result is a diagram that makes it possible to:
- Delimit what exactly is the perimeter of trust within the system.
- Establish how data transits between the different components and external entities.
- Understand which external entities are able to interact with the system and how they can do so, including the various access privileges.
- Visibility of where to apply specific security policies.
2. Identifying vulnerabilities
The development of a diagram facilitates the next step: determining what the asset's potential vulnerabilities are.
At this point, both the areas susceptible to vulnerability (due to a malicious attack, but also to accidents) and the type of known attacks that could be relevant to the system (code injection, DDoS attacks, etc.) are established.
Threat categorization methodologies such as STRIDE (described below) are useful here, as they provide a structure for establishing vulnerabilities; or the so-called threat trees, which structure possible threats in a hierarchical manner.
Risk mitigation
This involves taking the necessary measures to minimize the probability that the threats detected in the previous step will occur.
It is recommended that the implementation of these countermeasures, in addition, takes place by prioritizing the most urgent ones. This prioritization is done in a systematic way, taking into account the risk level of the threat, the probability of its occurrence and the complexity or cost of solving it. Again, some specific methodologies described in the following section are helpful in this process.
As a result in this step, the following responses can be determined:
- Threat mitigation, i.e., actions that seek to reduce the likelihood of a threat materializing are detailed.
- Elimination of components that potentially pose a threat.
- Risk transfer (e.g., generating user responsibility policies).
- Risk acceptance.
4. Ongoing verification and modeling
No threat modeling process is complete without verifying that the measures taken are effective against the cyber threats detected. Depending on the asset to be protected, an audit may be carried out, or the application may be run in a test environment. In any case, it is in the verification phase that questions such as the following must be answered:
- Has accurate visibility over the asset or system to be protected been obtained?
- Have all possible cyber threats been detected?
- Has an appropriate response to each threat been determined?
- Can the measures taken be tested to verify their effectiveness?
Moreover, the reality of threat modeling is that it must be understood as a continuous process that goes beyond a single assessment in the lifecycle of an application or an isolated cybersecurity action undertaken by a company.
In a digital environment where cyber threats are continuously evolving, multiplying and transforming, only an ongoing assessment is capable of generating a truly robust cybersecurity posture aligned with real risks.
Threat modeling techniques
There are a number of methodologies that aim to structure a part of threat modeling, serving as an outline in processes that can be highly complex. Although there is the possibility of developing one's own techniques and methodologies, the following are a useful starting point:
- STRIDE: designed by Microsoft, this methodology is based on classifying potential cyber threats into the following six categories:
- Spoofing (spoofing).
- Tampering (data manipulation)
- Repudiation (denial of action)
- Denial of Service (denial of service)
- Elevation of Privilege
Through these categories, it provides a structure for threat modelers to explore these six specific threat types in the asset. Six threats that, in turn, have associated with them certain controls to mitigate them.
- PASTA - an acronym for Process for Attack Simulation and Threat Analysis - provides a 7-step framework for identifying, quantifying and analyzing threats. Strengths include the focus of this methodology on the impact of threats on the business; the tools for modeling potential attackers; and the activation of attack simulation.
- VAST: again an acronym, in this case for Visual, Agile, and Simple Threat , this highly scalable methodology specializes in integrating into agile development processes. Regarding the visual part, this technique promotes the use of diagrams and graphical representations to make threat modeling more accessible; in addition, it seeks to perform threat assessments in short iterations, thus adapting to agile environments.
- DREAD: another threat modeling technique developed by Microsoft, in this case it is aimed at quantifying threats and then prioritizing their resolution by means of a scoring system that classifies them from most to least critical. To this end, it proposes the following scoring categories:
- Damage Potential (damage potential).
- Reproducibility (reproducibility)
- Exploitability (exploitability)
- Affected Users
- Discoverability (discoverability)
- OCTAVE: this methodology (developed by Carnegie Mellon University's CERT Coordination Center) seeks to focus on critical assets and processes for organizations, combining threat assessment with an understanding of business needs and their specific context. The name is an acronym for Operationally Critical Threat, Asset, and Vulnerability Evaluation.
- LIDDUN: in this case, the methodology focuses on privacy-related threats, helping to identify and mitigate them. For this purpose, this technique developed by KU Leuven establishes the following categories:
- Linkability (linkability)
- Identifiability (identifiability)
- Non-repudiation (non-repudiation)
- Detectability (detectability)
- Disclosure of information
- Unawareness
- Non-compliance
Benefits of threat modeling
- Security by design for the release of applications and software.
- Detection of problems or vulnerabilities and remediation at early stages and in a proactive manner, with the cost savings that this entails.
- Reduction of the attack surface through a systematic approach to detect vulnerabilities that other methodologies may not take into account.
- Tuning protection beyond “standard” threats by tailoring the process to the actual needs of the asset or organization and identifying specific security requirements.
- Increased collaboration capabilities through amplified visibility.
- Facilitates data-driven cybersecurity decision-making, including decisions around threat mitigation prioritization and cybersecurity resource allocation.
- Capabilities to prove the security posture of the asset or organization, through specific documentation.
- Strengthening compliance with privacy and security legislation.
In short, threat modeling should be understood as one of the fundamental pillars of the cybersecurity strategy in any organization or development.
At S2 Grupo, we are committed to helping organizations seeking to cope with an increasingly hostile digital landscape.
In this regard, among our portfolio of cybersecurity solutions we include our Threat Intelligence solution. Based on the advanced cyber intelligence of our Lab group52, we offer advanced threat analysis services using technology developed in-house with the National Cryptologic Center ( CCN) to identify anomalies.
Thanks to the support of our team of expert analysts, we travel to organizations' sites to assess the threats they are exposed to and implement measures to mitigate them.
We also have two highly advanced tools for the development of threat modeling protocols:
- Carmen: tool for the detection of advanced cyber-attacks, aimed at facilitating the process of detecting anomalies and misuse.
- Claudia: Endpoint solution for the detection of complex malwaresand lateral movements linked to advanced persistent threats (APT).
All backed by advanced cyber threat intelligence to detect problems at an early stage and stay ahead of potential attackers.
Do you want to know more about threat modeling and how to implement it in your organization? At S2 Grupo we can help you. Contact us and talk to our team.
